[ad_1]

Researchers have warned of a spike in exploit attempts weaponized against critical remote code execution flaws in the Realtek Jungle SDK since early August 2022.
According to Palo Alto Networks Unit 42, the ongoing campaign has recorded 134 million exploit attempts as of December 2022, with 97% of attacks reportedly occurring in the last four months. I’m here.
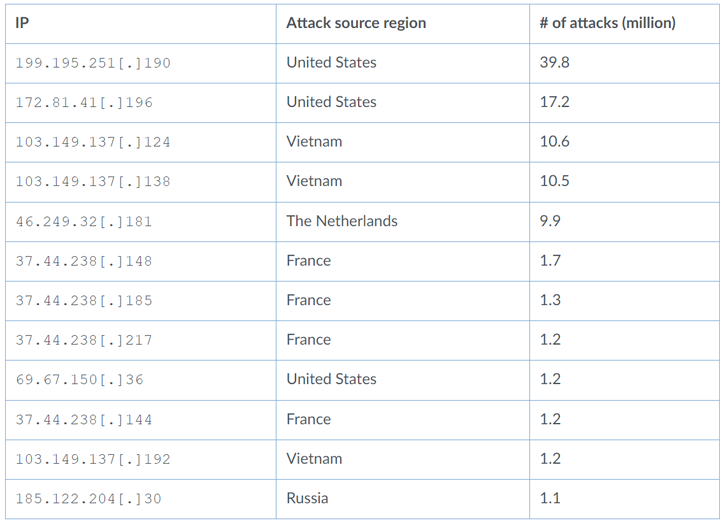
Nearly 50% of attacks originated from the United States (48.3%), followed by Vietnam (17.8%), Russia (14.6%), Netherlands (7.4%), France (6.4%), Germany (2.3%0, Luxembourg (1.6%) %).
Additionally, 95% of exploited security flaw attacks originating from Russia identified Australian organizations.
“Many of the attacks we observed attempted to deliver malware to infect vulnerable IoT devices,” Unit 42 researchers said in a report, noting that “threat groups have exploited this vulnerability to , is conducting massive attacks against smart devices around the world,” he added.
The vulnerability in question is CVE-2021-35394 (CVSS score: 9.8), a series of buffer overflow and arbitrary command injection bugs that can be weaponized to execute arbitrary code with highest privileges and affect can hijack appliances that receive
This issue was disclosed by ONEKEY (formerly IoT Inspector) in August 2021. This vulnerability affects a wide range of devices from D-Link, LG, Belkin, Belkin, ASUS, and NETGEAR.
Unit 42 said it discovered three different payloads being distributed as a result of this vulnerability being exploited in the wild.
- The script executes shell commands on the targeted server and downloads additional malware
- An injected command that writes a binary payload to a file and executes it.
- Injected commands that cause a denial of service (DoS) condition by directly rebooting the target server
Exploitation of CVE-2021-35394 also delivers known botnets such as Mirai, Gafgyt, Mozi, and a new Golang-based distributed denial of service (DDoS) botnet called RedGoBot.
The RedGoBot campaign, first observed in September 2022, contains a shell script designed to download numerous botnet clients tuned for different CPU architectures. Once launched, the malware has the ability to execute operating system commands and launch DDoS attacks.
The findings once again underscore the importance of timely software updates to avoid exposure to potential threats.
“The surge in attacks leveraging CVE-2021-35394 shows that attackers are very concerned about supply chain vulnerabilities that are difficult for the average user to identify and remediate. There are cases,” the researchers conclude. “These issues may make it difficult for affected users to identify the specific downstream product being exploited.”
[ad_2]
Source link
