[ad_1]

A shellcode-based packer called trick gate It has been operating under the radar for over six years while enabling threat actors to deploy a wide variety of malware including TrickBot, Emotet, AZORult, Agent Tesla, FormBook, Cerber, Maze, and REvil.
Check Point Research’s Arie Olshtein called TrickGate a “master of disguise” and said, “TrickGate has been kept under the radar for years because it’s a game-changer. It’s changing,” he said.
TrickGate has been available as a service to other threat actors since at least late 2016, helping to hide payloads behind layers of wrapper code in an effort to evade security solutions installed on hosts. . Packers also act as crypters by encrypting malware as an obfuscation mechanism.
“Packers have a range of capabilities that allow them to appear as benign files, make them difficult to reverse engineer, and incorporate sandbox evasion techniques to evade detection mechanisms,” Proofpoint said December 2020. points to the moon.
However, with frequent updates to the commercial packer-as-a-service, TrickGate has been tracked under various names since 2019, including new loaders, Loncom, and NSIS-based crypters.
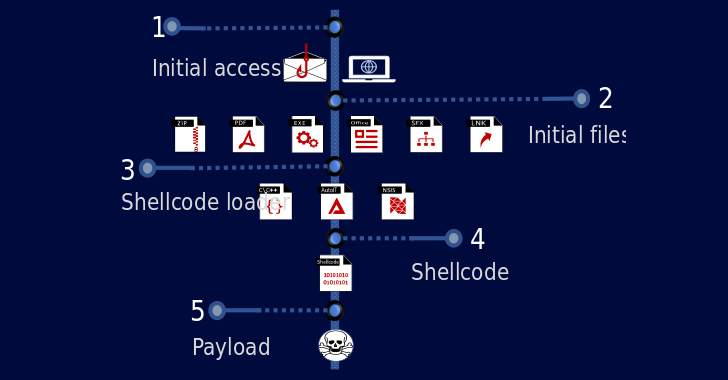
Telemetry data collected by Check Point shows that the TrickGate attackers primarily singled out the manufacturing sector, and to a lesser extent the education, healthcare, government, and financial sectors.
The most common malware families used in attacks over the past two months included FormBook, LokiBot, Agent Tesla, Remcos, and Nanocore, with significant concentrations reported in Taiwan, Turkey, Germany, Russia, and China It has been.
Phishing emails containing malicious attachments or booby-trapped links are sent up the infection chain to download a shellcode loader that decrypts the actual payload and launches it into memory.
An analysis of the shellcode by an Israeli cybersecurity firm shows that “although it has been constantly updated, key functionality is present in all samples since 2016.” It is a sensitive part and has been observed in all TrickGate shellcodes.”
[ad_2]
Source link

