[ad_1]
For developers who want to benefit from Google’s commitment to security, a service that allows developers to use open source components that they know have been vetted and patched for security issues by Google developers. you will be able to join immediately.
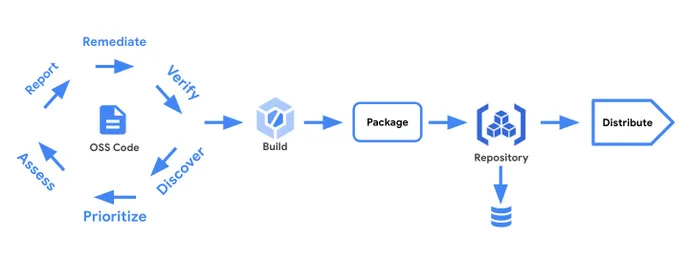
Called Assured Open Source Software (OSS), the service is frequently scanned, augmented with metadata produced by code analysis, conforms to the early Supply chain Levels for Software Artifacts (SLSA) framework, and is signed. Provides versions of popular open source packages that are available. by.
In many ways, the service resembles the curated Linux distributions maintained by companies such as Red Hat and Ubuntu, said Eric Brewer, vice president of infrastructure at Google Cloud and a Google fellow. I’m here.
“The idea of having a curated version isn’t new per se, but it’s more important than ever,” he says. “Plus, I wanted to show that it’s important to actually look at provenance, create metadata, scan, fuzz, build from source and sign. That’s the right way to go.”
The announcement of this new service comes a week after the Linux Foundation and the Open Software Security Foundation announced plans to protect open source software, backed by nearly 40 companies. Its efforts are focused on ten separate initiatives in three broad areas: securing open source products, improving vulnerability discovery and remediation, and accelerating patch cycles.
Google was a major sponsor of this effort, and has contributed technology and specifications to countless security-focused initiatives, including Security Scorecards, AllStars, and the Alpha Omega Project, but OSS eventually became a paid commercial service. I’m sure it will be Say.
“Last week was about community focus,” says Brewer. “But you… [also] To make them better and easier to use, we need a lot of private investment from various companies, and a lot of industry cooperation, especially for the critical core part. “
Scanning, fuzzing and checking on 100K cores
Most companies maintain their own package management systems as private repositories, but when you look at the numbers, Google’s level of vetting and security testing matters.
In a blog post announcing its Assured OSS service, Google said the company uses a massive infrastructure based on 100,000 processor cores to deliver end-to-end, including continuous fuzzing of over 500 of the most popular packages. It is said that there is a process of The company also offers a software bill of materials (SBOM) and an integrity check of his chain of supply through the SLSA framework.
The Assured OSS framework also natively integrates with Snyk, a software security analytics company.
Google Cloud said in a blog post: “Instead, development teams independently decide how to redistribute third-party source code and packages within their organization, depending on where they get their source code and packages, how they build, and their goals, threat and risk models, and resources. There is a possibility.”
Duplicate Efforts Bring Inefficiency Risk
Google isn’t the only company offering a curated, curated collection of open source software. In addition to the aforementioned Linux distributions, various companies such as Anaconda create vetted repositories that include managing both corporate patching and integrity issues. Additionally, other companies such as Snyk, Sonotype, and Debricked provide methods for evaluating open source projects and libraries based on security metrics.
But Google’s new service, which offers overlapping services where multiple companies offer similar analysis of the top 500 packages, is likely to skip the review of less popular but still important packages. causes anxiety. Redundancy is often a good attribute, as a company may discover vulnerabilities missed by another company, but it is also important for organizations to provide more coverage across more packages. , Brewer admits.
“There are many ways to work together, but I think open source by its very nature is already shared, so we need to work more collaboratively,” he says. “So at least you should make sure you’re fixing different packages instead of fixing the same package. It’s globally inefficient to do that.”
According to Google, Assured OSS will be available for preview in the third quarter of 2022.
[ad_2]
Source link
