[ad_1]
Frameworks are convenient skeletons of structs or methods. It is policies, procedures, theoretical knowledge, and practical application that provide guidance on actions to take and deliver better results faster.
A cybersecurity framework is a framework defined by a cybersecurity organization to determine a cybersecurity strategy for an enterprise environment. A cybersecurity framework enhances existing security protocols and creates new layers of security when they are not available. It detects unknown security vulnerabilities in corporate networks and tries to reduce misconfigurations. Here are five that you can find across the industry.
1. Credit card industry data security standards
Payment Card Industry (PCI) is a cybersecurity standard designed to enhance the security of payment transactions made from credit and cash cards in banking transactions. PCI includes logical and physical data security standards that must be adhered to while processing, transmitting, and storing transactions made from credit and cash debit cards. The credit card industry strives to standardize data security, reduce data security-related risks, create an environment of trust, and protect cardholders. This standard should generally provide:
- Credit and cash card customer information in a secure network
- System password and complexity settings
- Sending credit and cash card customer information over encrypted connections
- Use and update antivirus software on your system
- Continuous monitoring and recording of access to card information
- Physical protection of data centers with information
2.ISO27001
ISO 27001 is the International Organization for Standardization’s governing framework for defining analytics and addressing information security risks. The implementation of ISO 27001 procedures will enable institutions to be resilient to cyberattacks, adapt to changing threats, reduce costs related to information security, and reduce the costs of information security and the people, processes, and protection of all data. and provide policy procedures and controls, including technology.
3. Important security controls
Critical security controls contain a set of rules that an organization must follow in order to create an effective cybersecurity strategy. These security controls define her three groups of critical security controls that organizations must comply with. These are simple, basic, organized sets of controls. What these three different sets of controls have in common is taking precautions to protect your data and minimize the potential for attacks. Many measures fall under these control sets, from email and web browser protection to vulnerability scanning tools and even network device security.
The fact that these boundaries and precautions are predetermined and that there are certain rules for everything minimizes the chances of making mistakes within an organization. can lead to poor results. So everything to check is prepared in advance. You can think of them like cybersecurity precautions for your organization.
4. National industry standards and technology
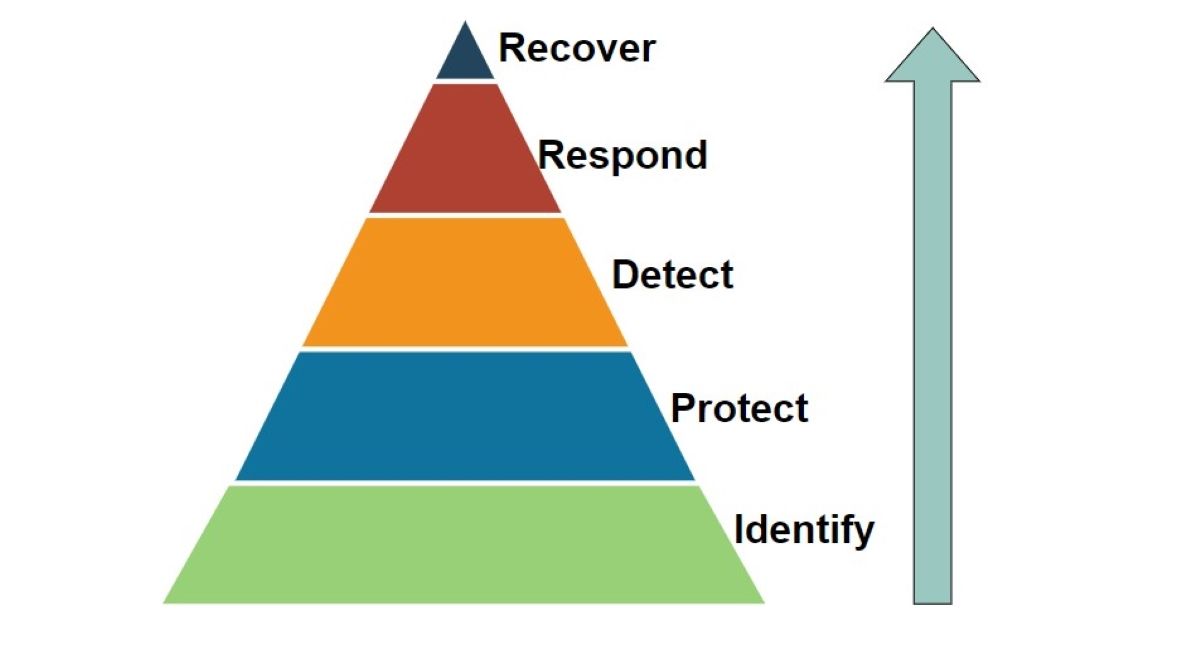
There is a cybersecurity framework called NIST that is used by US civilian organizations. This framework provides several policies on how to take action before a cyberattack occurs. It is also a guide on how to detect attacks and how to respond to them. Not only the United States, but also the governments of countries such as Japan and Israel use NIST. To fully understand this guiding policy, we need to consider his five main functions it provides.
- identification: Managing cybersecurity risk requires an enterprise approach to managing systems, assets, data, and functions within an organization.
- protect: Organizations should develop and implement appropriate recommendations to limit potential cybersecurity incidents or impacts.
- detection: Organizations must implement appropriate measures to identify cybersecurity incidents. Detect anomalous activity and threats to continuity of operations and employ monitoring solutions.
- response: When a cybersecurity incident occurs, organizations must contain its impact. This requires the organization to prepare a cybersecurity incident response plan, identify communication failures between appropriate parties, gather information about the incident, and analyze this information.
- recovery: Organizations should have a recovery plan for services damaged by a cybersecurity incident. When developing this rescue plan, all experiences learned after the attack should be taken into account and the plan updated accordingly.
5. MITER ATT&CK Framework
The MITER ATT&CK framework is a very comprehensive cybersecurity framework used by both the red and blue teams. There is a knowledge base and classification of aggressive behavior. It doesn’t focus on tools or malware used by competitors. Examine how attacks interact with the system during operation. The ATT&CK framework is a fairly large knowledge base for modeling aggressive behavior. The following concepts can be associated with this framework:
- A malicious group carries out an attack.
- Institutions and industries targeted by attackers or aggressive groups.
- Attack vectors and attack types used by attackers.
- The steps malicious attackers follow to attack.
- Method of attack detection. For example, you might be monitoring a network for anomalies, or have permissions on a system that shouldn’t exist.
- countermeasures against attacks. For example, you can consider measures such as two-step verification, firewalls, use of antivirus, and code signing.
The ATT&CK cybersecurity framework has a very large data pool and is constantly being updated. In addition, in light of all the important information it offers, it not only provides server or computer network security, but also very important information about mobile security. Being able to see this information and predict how a potential attack might work is a big plus. If you are new to the world of cybersecurity and you are at the forefront of everything, the ATT&CK framework will be a wealth of information.
Will these frames solve everything?
No. Hundreds of new types of attacks and malware appear every day, even every hour. But if you’re managing a project with millions of lines of code, or trying to protect the banking information of hundreds of thousands of people, you’ll need to follow a systematic and political process. These cybersecurity frameworks can be very helpful in this regard.
But these frames are just skeletons. A lot more is needed to complete the exterior. If you don’t know where to start, I recommend studying the NIST framework to learn more about it.
[ad_2]
Source link