[ad_1]
A subcategory of BEC, Financial Supply Chain Compromise, appears to be prevalent and highly effective. Abnormal Security has identified one malicious actor in his name, Firebrick Ostrich. It uses subtypes of these tricks to trick the target into paying.
The company had previously identified four types of financial supply chain breaches that impersonated one of the targeted company’s vendors without impersonating an internal executive of the company. According to Abnormal Security, Firebrick Ostrich used one of these types of financial supply chain compromise (a third-party reconnaissance attack) to carry out 346 BEC campaigns dating back to April 2021, Impersonated 151 organizations and used 212 maliciously registered domains.
Crane Hassold, director of threat intelligence at Abnormal Security, said that the amount of money coming from outside third-party impersonation was three times higher than traditional BEC exploits, and its success was attributed to a lack of awareness as a company and its employees. said to be due to They are trained to look for emails impersonating internal executives rather than vendors.
“Also, when looking at third-party reconnaissance and other financial supply chain attacks, the effectiveness of lures hinges on the amount of information that can be put into an email. It makes it look realistic to the BEC,” he said.
look: Mobile device security policy (TechRepublic Premium)
Hassold says tens of billions of dollars are lost to BEC each year and BEC is the leading cause of economic losses for businesses dating back to 2016.
“BEC has actually exploded, peaking in the first six months of last year, due to attackers masquerading as external entities. Since its inception, it has mainly involved the impersonation of internal entities,” he said. “BEC actors have identified third parties, including vendors, as weak points in the chain.”
Jump to:
Big profits from low-tech spoofing
From a cybercrime-as-a-business perspective, the overhead required to launch a third-party reconnaissance attack is low, Hasold said. It requires basic reconnaissance and intelligence gathering, and does not require the underlying infrastructure or developers to maintain and enhance the malware. “It’s just sending emails, so from an overhead perspective, it’s very advantageous,” he said.
According to Abnormal, third-party spoofing exploits, most of which originate from West Africa, use a three-step process (Figure A).
Figure A
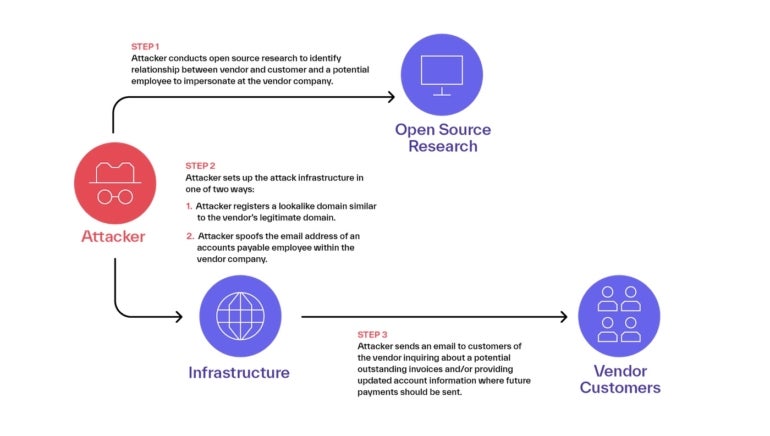
- open source research For vendor customer relationships, check state and local governments that provide detailed information about existing and previous contracts, or vendor websites where companies display the customer’s name or logo, or possible connections can be obtained from googling the company name to
- Attack infrastructure: This group registers domains using Namecheap or Google as registrars impersonating vendor domains, impersonating email addresses of accounts payable employees within vendor companies.
- Targeted emails to customers: Attackers email vendors’ customers to inquire about potential unpaid invoices or provide up-to-date account information to which future payments are sent.
Attack within a week after domain name registration
Firebrick Ostrich’s use of newly registered domains, combined with other behavioral indicators, highlights how new domains can be used as effective signals to identify threats, according to Abnormal Security. . Abnormal Security reported that 60% of domains registered by Firebrick Ostrich were registered on the same day as the BEC campaign run they were deployed. About three-quarters of the domains were acquired within 48 hours of the attack, and 89% of the domains were registered within one week of the campaign.
look: Here’s how IT budgets will fill the cybersecurity moat in 2023. (Tech Republic)
Firebrick Ostrich uses newly registered domains to create email addresses impersonating real vendor account staff to facilitate attacks. The primary account mimics the vendor’s actual accounts receivable clerk to communicate with the target. A secondary email account, which can include the vendor’s financial executives, adds a layer of credibility to their attacks, according to the company.
“Reasonable” demands and long game tactics
According to Abnormal Security’s report, the initial emails of Firebrick Ostrich attacks typically begin with a greeting from the vendor, something like “Thank you very much for being our valued customer. Thank you for your continued support.” two requests may follow.
- The first request indicates that the vendor wants to update the bank account on file for the customer. The email points out that the vendor cannot accept payments by check, so ACH and wire transfer payments are the only options available.
- The second request inquires about outstanding payments to the vendor. The email states that the vendor can no longer track open invoices because the accounting team is unable to verify the account. Firebrick Ostrich provided details in one of his emails, saying the account team was “unable to access servers or Oracle to verify your account or post any payments you may have received.” said.
“The technical problem hoax excuse, a common excuse used in many third-party reconnaissance attacks to explain why vendors cannot access their invoice inventory, is shown here. The compliments being given seem unique to this BEC group,” said Hassold.
Because another tactic is simply to update the vendor’s stored bank account details so that future payments are redirected to the new account instead of requiring payment of the current bill. , is particularly clever. According to Abnormal Security, this avoids red flags that accounts payable professionals may be trained to notice. The longer game is that threat actors get paid on the next bill, not the actual vendor.
What makes this group so unique is that they have been able to achieve great success without having to compromise accounts or conduct in-depth research into vendor-customer relationships. According to Abnormal Security, using some pretty obvious social engineering tactics can uncover everything you need to run a successful BEC campaign. There is no need to invest significant time and resources in initial research.
Holistic screening is the best defense
Hassold said email flagging techniques that identify static indicators are insufficient to defend against BEC attacks. He recommended using techniques such as behavioral analysis to understand the relationship between senders and receivers for more holistic defense. This holistic strategy also incorporates information about the target company’s third parties his vendor his ecosystem and monitors both specific impersonation attacks impersonating those vendors and suspicious language and artifacts.
“It is important to understand what trends we see across the cyber threat landscape and make sure employees are aware of these,” he said. “This means that if you see a Firebrick Ostrich-style attack with a request to change an account or a message about a technical issue, you may have an in-house effort to validate those requests offline with the vendor well before the change is actually made. The policy is already in place: We think of cyberattacks as very sophisticated, but at the end of the day, they are mostly just social engineering, trying to manipulate human behavior.
With cybersecurity attacks likely to rise this year and threat actors becoming more sophisticated, it’s also a good time to wear a white hat. Learn the ropes for $30 with nine ethical hacking courses from TechRepublic Academy.
[ad_2]
Source link

